GAMP-5 guidance, the related “V model” and the different software categories used to simplify the validation activities are nowadays considered the internationally recognised best approach for computer system validation. GAMP stays for “Good Automated Manufacturing Practice” and it is a guideline which is published by the ISPE, International Society for Pharmaceutical Engineering. The guideline is currently in Version 5.
Good Automated Manufacturing Practice, Founded in 1991. International Society for Pharmaceutical Engineering (ISPE) sets the guidelines for manufacturers and the current Version is GAMP 5.
GAMP-5 is very important especially when the software application is provided by a supplier external to the organization. In fact this regulation requires users and suppliers to work together, each of them according to specific responsibilities, two gain the full validation of the software system.
Specifically, for the users, GAMP-5 provides a framework for validation activities to ensure that the system is fully validated according to its intended user before it moves to production. Suppliers, at the same time, can use GAMP to test the SW application for avoidable defects in the supplied system to ensure quality products are produced.
The Principles of GAMP-5 Guidelines
The GAMP-5 guideline for computer system validation is built upon a set of five fundamental principles, which serve as pillars for ensuring the integrity and compliance of computerized systems within regulated industries. Let’s delve into each of these principles in detail:
- Product and Process Understanding: The first principle emphasizes the importance of thoroughly comprehending both the product being developed or manufactured and the underlying processes involved. This understanding is crucial for effectively validating computer systems that are integral to these products and processes. By gaining a deep insight into the product’s intended use, critical quality attributes, and associated manufacturing or operational processes, organizations can make informed decisions regarding system design, qualification, and validation.
- Lifecycle Approach within QMS: The second principle advocates for the adoption of a lifecycle approach to computer system validation within the Quality Management System (QMS) of an organization. This means that validation activities should be planned, executed, and documented throughout the entire system’s lifecycle, from concept and development to retirement. Implementing a systematic and structured approach ensures that the validation process is consistent, traceable, and compliant with regulatory requirements.
- Scalable Lifecycle Activities: The third principle highlights the need for scalability in conducting validation activities. It recognizes that the extent and rigor of validation should be commensurate with the level of risk associated with the system and its intended use. This principle encourages organizations to evaluate the complexity, criticality, and impact of the computer system on product quality, patient safety, and data integrity. By adopting a risk-based approach, resources can be allocated appropriately to focus efforts on areas of higher significance, while ensuring a streamlined and efficient validation process.
- Science-Based Quality Risk Management: The fourth principle underscores the integration of quality risk management principles into computer system validation. It emphasizes the application of scientific and risk-based methodologies to identify, assess, control, and communicate risks associated with the use of computerized systems. By proactively addressing potential risks and implementing risk mitigation strategies, organizations can enhance the reliability, security, and compliance of their computer systems.
- Leveraging Supplier Involvement: The fifth principle recognizes the importance of involving suppliers in the validation process. It acknowledges that computer systems often rely on external suppliers for components, software, or services. Effective collaboration with suppliers ensures that the systems provided meet the necessary quality, functionality, and regulatory requirements. By establishing clear expectations, requirements, and communication channels with suppliers, organizations can foster a partnership that supports the successful validation and ongoing maintenance of computer systems.
Product and Process Understanding
In order to successfully conduct a validation activity, a comprehensive understanding of both the software product and its associated processes is imperative. The validation process culminates with the issuance of a “Fit for Use” statement, which can only be confidently provided if the most crucial functionalities of the product have been thoroughly comprehended and rigorously tested. These critical functionalities encompass aspects that significantly affect patient safety, product quality, and the security and integrity of data.
By delving deep into the intricacies of the software product, one can discern the functionalities that hold paramount importance in ensuring the overall success and effectiveness of the system. These critical functionalities act as the cornerstone for establishing a robust validation process. They encompass features and capabilities that, when functioning optimally, contribute directly to the safety and well-being of patients, the consistent delivery of high-quality products, and the protection of sensitive data.
Ensuring that the critical functionalities are comprehensively understood and rigorously tested is crucial for validating the software product’s suitability for its intended purpose. This involves a meticulous examination of how these functionalities interact with other system components, how they contribute to the overall product performance, and how they align with regulatory requirements and industry standards. Additionally, it necessitates conducting comprehensive testing to verify their reliability, stability, and accuracy under various operating conditions.
By focusing on the critical functionalities during the validation process, organizations can effectively mitigate risks associated with software failures or deficiencies that could have severe consequences for patients, product quality, and data security. It enables thorough scrutiny of these essential aspects, fostering a systematic approach to validation that ensures compliance with regulatory guidelines and industry best practices.
Ultimately, a successful validation activity hinges on the comprehensive understanding and meticulous testing of the critical functionalities within the software product. This approach empowers organizations to confidently assert the system’s fitness for use, assuring stakeholders that the product has been thoroughly evaluated and meets the highest standards of safety, quality, and data integrity.
Lifecycle approach within QMS
The effective management of computer systems throughout their lifecycle is a critical aspect of the validation process, and it necessitates integration within the organization’s quality management system. As prescribed by the GAMP-5 methodology, this entails the establishment of a comprehensive Standard Operating Procedure (SOP) that outlines the management approach for each stage of the software application’s lifecycle.
By incorporating all phases of the software lifecycle into the quality system, organizations can demonstrate their commitment to ensuring adherence to defined requirements at each stage. This integration facilitates a seamless flow of activities, beginning from the conceptualization phase, where requirements are meticulously delineated, through to the subsequent stages of release, maintenance, and eventual retirement of the software.
During the concept phase, organizations must meticulously define and document the software’s functional and non-functional requirements. These requirements serve as a blueprint for the development and validation activities that follow. By explicitly outlining these requirements within the quality management system, organizations establish a robust foundation for the subsequent stages of the software’s lifecycle.
To effectively manage the release, maintenance, and retirement of the software, organizations must develop detailed SOPs that provide clear guidance and instructions for these specific stages. The release phase entails activities such as software installation, configuration, and documentation, which must be carried out systematically and in compliance with established procedures. Similarly, the maintenance phase encompasses ongoing support, bug fixes, and periodic updates to ensure the software’s continued functionality and reliability. Finally, the retirement phase necessitates proper decommissioning procedures, data migration or archiving, and the identification of any potential risks associated with the cessation of the software’s use.
By meticulously documenting and adhering to SOPs that encompass the entire software lifecycle, organizations can demonstrate their commitment to ensuring quality and regulatory compliance. This comprehensive approach provides a solid foundation for effective validation activities, as it ensures that all necessary requirements are defined, managed, and monitored throughout the software’s lifecycle.
Scalable Lifecycle Activities
The scaling or modeling of lifecycle activities for the validation of a software application can be approached from various perspectives, taking into consideration different parameters that influence the process. These parameters include:
- System impact on patient safety, product quality, and data integrity: The level of risk associated with the software application’s impact on patient safety, product quality, and data integrity plays a significant role in determining the extent of validation activities. A thorough risk assessment is conducted to identify and evaluate potential risks and their consequences, enabling the validation efforts to be tailored accordingly.
- System complexity and novelty: The complexity and novelty of the software application also influence the validation approach. Complex systems with intricate functionalities may require more extensive validation activities compared to simpler ones. Similarly, novel technologies or unique functionalities may necessitate additional validation efforts to ensure their reliability and compliance.
- Outcome of supplier assessment: The assessment of the software application’s supplier and their adherence to quality standards and regulatory requirements is an important consideration. The outcome of this assessment informs the level of confidence placed in the supplier’s deliverables and may influence the extent of validation activities required.
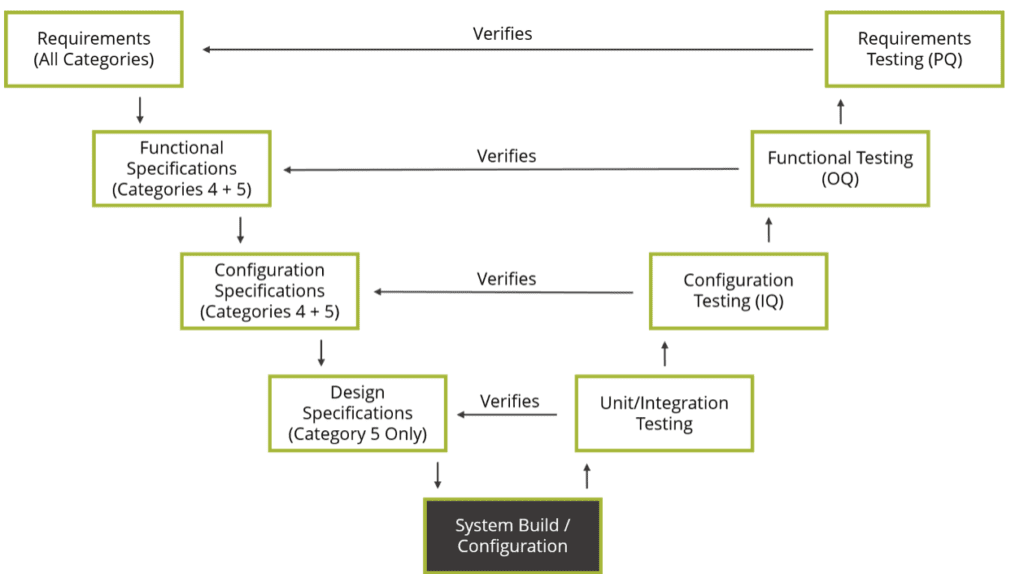
The V model, which serves as a reference for the software application’s lifecycle model in accordance with GAMP-5, provides a structured framework for conducting validation activities. Within this model, different GAMP-5 categories are utilized to classify software applications based on their characteristics, and the validation efforts are tailored accordingly. For a detailed description of these categories, you can refer to procedure P-06: Computer System Validation.
It is important to note that the V model can be flexibly adjusted or modified to align with the specific parameters mentioned above. GAMP-5 emphasizes that the type and extent of validation requirements associated with a system should be commensurate with its level of novelty and complexity, which, in turn, is reflected in the assigned GAMP-5 category.
Science Based Quality Risk Management
The GAMP-5 methodology advocates for focusing validation efforts on the most critical functions of a software application. To identify these critical functions, a risk management approach is recommended, emphasizing the importance of comprehending both the product and the associated processes. This understanding is essential for assessing potential risks to patient safety, product quality, and data integrity accurately.
To effectively apply the risk management approach, organizations are advised to follow a systematic and stepwise process, which includes the following sequential steps:
- Identify functions that have a direct impact on patient safety, product quality, and data integrity. These functions are of paramount importance as they are closely linked to critical aspects of the software application.
- Perform comprehensive functional risk assessments for the identified functions. This involves evaluating the potential risks associated with each function, considering factors such as system behavior, data processing, and user interactions.
- Implement and verify appropriate controls to mitigate identified risks. This step involves implementing measures, controls, or safeguards to address the identified risks effectively. Verification activities are conducted to ensure the adequacy and effectiveness of these controls.
- Continuously review risks and monitor the implemented controls throughout the lifecycle of the software application. Regularly reassessing risks allows for timely identification of any new risks that may emerge during development, deployment, or operation. Monitoring the implemented controls ensures their ongoing effectiveness and highlights any areas requiring adjustments or improvements.
For detailed guidelines on how to implement functional risk assessments, organizations can refer to the Computer System Validation procedure P06. This procedure provides a structured methodology and specific instructions for conducting thorough functional risk assessments within the context of computer system validation.
Leverage the involvement of the supplier
In accordance with the GAMP-5 guidelines, the organization holds the ultimate responsibility for conducting the validation of the software application they utilize. Nevertheless, regulated companies have the opportunity to capitalize on their suppliers’ documentation, which may include valuable test documentation, in order to prevent unnecessary efforts and redundant tasks. The key to successful validation lies in fostering collaboration between the suppliers and the organization responsible for the validation process, as this partnership is essential for ensuring that the validation efforts are purposeful and effective.
By leveraging the supplier’s documentation, the organization can benefit from pre-existing test documentation, which can serve as a valuable resource in the validation process. This approach not only saves time and resources but also avoids duplicating efforts that have already been undertaken by the supplier. It allows the organization to focus their validation activities on areas that require specific attention and customization to meet their specific needs and regulatory requirements.
However, it is important to note that relying solely on the supplier’s documentation is not sufficient. The organization must actively participate in the validation process and contribute their expertise and insights. Collaboration between the supplier and the organization is crucial in order to establish a mutual understanding of the software application and its intended use, as well as to address any specific requirements or concerns related to the organization’s operations.
Through effective collaboration, the supplier can provide valuable insights into the software application’s functionalities, performance, and potential risks. They can also assist in clarifying any ambiguities or uncertainties in the documentation, ensuring a comprehensive and accurate understanding of the software’s capabilities and limitations. This collaborative approach enhances the overall quality and reliability of the validation efforts.
Furthermore, open and transparent communication between the supplier and the organization is vital throughout the validation process. Regular meetings, discussions, and documentation exchanges enable the parties to align their expectations, resolve any issues or discrepancies, and ensure that the validation activities are conducted in a coordinated and harmonious manner.
Subscribe to 4EasyReg Newsletter
4EasyReg is an online platform dedicated to Quality & Regulatory matters within the medical device industry. Have a look to all the services that we provide: we are very transparent in the pricing associated to these consulting services.
Within our WebShop, a wide range of procedures, templates, checklists are available, all of them focused on regulatory topics for medical device compliance to applicable regulations. Within the webshop, a dedicated section related to cybersecurity and compliance to ISO 27001 for medical device organizations is also present.
As one of the leading online platforms in the medical device sector, 4EasyReg offers extensive support for regulatory compliance. Our services cover a wide range of topics, from EU MDR & IVDR to ISO 13485, encompassing risk management, biocompatibility, usability, software verification and validation, and assistance in preparing technical documentation for MDR compliance.
Do not hesitate to subscribe to our Newsletter!

